Recently, we looked at the rsync command for syncing files between locations, and we discussed the similarity of usage and syntax when duplicating files and directories with the cp command. In that article, we looked at moving the bits back and forth on the same box, between filesystems, or between devices. In an upcoming article, we'll look more at rsync as a tool to keep remote filesystems in sync with a local or backup version. In this article, I want to take a look at one of the most useful and used tools in the Linux sysadmin toolbox—the scp command.
What is SCP?
The SFTP acronym actually stands for SSH File Transfer Protocol and is not used in the protocol specification. SCP – a variant of BSD rcp utility that transfers files over an SSH session. The SCP protocol has been mostly superseded by the more comprehensive SFTP protocol and some implementations of the scp utility actually use SFTP instead. Telnet, ftp, ssh and scp. In this module we will explore tools for connecting to other computers, downloading and uploading files. Telnet is a Unix utility that lets you login to another computer on the Internet provided you have an account on that computer. This can be especially useful if you work part time and wish to login to the. The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line, login, and remote command execution, but any network service can be secured with SSH. SSH provides a secure channel over an unsecured network by using a client–server architecture, connecting an SSH client.
Linux Security
Secure Copy, or scp, is a secure version of the older rcp tool (which is still used, but less common) included in the OpenSSH suite of tools.
OpenSSH started as a BSD fork of the original SSH secure communications protocol, which has since become re-licensed as 'non-free' and thus not generally available for Linux. OpenSSH is still maintained under the BSD license and is available for a wide range of platforms. It includes several common tools for secure remote access, including key generation, scp, and sftp (a secure version of FTP, which we'll get to in a bit).
Recently, OpenSSH developers have indicated that they consider scp to be deprecated (they believe it is 'Outdated, inflexible and not easily fixed'). It is unclear when it will cease to be available in future releases of OpenSSH, though it's hard to imagine that it will be dropped anytime soon.

Use SCP
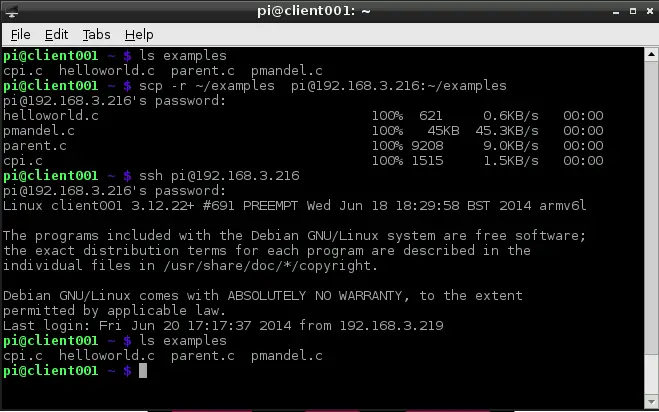
The usefulness of scp lies in its simplicity. I use it to quickly move files to a remote filesystem from the shell:
Easy as pie. I can get a file from a remote location, too:
The available connection options are the same as with ssh. For example:
-P specifies the port for the ssh connection, -i specifies an ssh id key to use for authentication: Both these options are useful for scripts. Note that the scp -P differs from the ssh -p for specifying the port. In the example above, I set the location of an ssh key (~/.ssh/id_rsa)—which I also generated using the OpenSSH toolkit—to authenticate access to the remote device. Learn about SSH file copies here.
So you can see scp is a really useful tool to have at your fingertips. There is some discussion of the wisdom of using this tool in a secure environment, so YMMV. I'd suggest doing some reading and deciding for yourself.
[ You might also like: Sysadmin tools: Using rsync to manage backup, restore, and file synchronization ]
Alternatives
What if, for whatever reason, we can't use scp? I recommend two other options that are pretty easy to use: rsync, which we have talked about here and will discuss in more depth in another article, and sftp. While neither of these options is as convenient as scp, both have some useful features.
sftp is pretty much what it sounds like: Secure FTP. It acts like FTP over an SSH-managed connection. While it's not as simple to use as the 'one and done' scp command, it offers a range of more sophisticated filesystem options and the ability to connect to a remote filesystem interactively. It does require that the target filesystem be configured for sftp access.
Let’s connect to an sftp server interactively:
If we hit Tab twice, we can see a list of commands available at the shell:
So you can see it's possible to interact with the remote filesystem. Again, the main disadvantages are the target has to be configured for sftp access and access to a specific directory has to be configured and limited by the admin of that system. This makes it a more secure, if less convenient, option than scp. Also, note that while it's not really possible to do impromptu file transfers like scp, it is possible to write scripts and insert shell aliases to make this work more smoothly if that's your jam.

[ Thinking about security? Check out this free guide to boosting hybrid cloud security and protecting your business. ]
Wrap up
Final note: Both these tools rely on the SSH toolbox, which is a very important part of Linux systems administration, so I highly recommend getting comfortable with it. Consider these excellent articles by Enable Sysadmin writers:
Check out these related articles on Enable Sysadmin
Overview
The aim of this article is to provide an introduction to some useful programs in the SSH2 suite, i.e. sftpandscp. In the following we suppose that the SSH2 daemon is well configured and running. You may check this on RedHat Linux:
$ rpm -q openssh
openssh-3.1p1-6
Configuration
The first one (Secure File Transfer) is a ftp-like client that can be used in file transfer over the network. It does not use the FTP daemon (ftpd or wu-ftpd) for connections, allowing a significant improvement in the system security. The use of sftp prevents all hacker attacks since it permits to stop the potentially dangerous wu-ftpd.
The second (Secure Copy) is used to copy files over the network securely. It is a replacement for rcp insecure command.
Sftp and scp do not require any dedicated daemon since the two programs connect to sshd servers. In order to use sftp and scp you have to insert the following line in the configuration file /etc/ssh/sshd_config(RedHat Linux).
Subsystem sftp /usr/libexec/openssh/sftp-server
After this modification you must restart sshd. So you could use sftp and scp only to connect to hosts where sshd is running.
SFTP
Sftp uses SSH2 in data connections, so the file transport is as secure as possible. There are two main advantages in using sftp instead of ftp:
Password are never transferred in clear text, preventing any sniffer attack.
Data are encrypted during the transfer, making difficult to spy or modify the connection.
The use of sftp is really simple. Let's suppose that you would connect via sftp to your account zahn on host1. In order to do that use the command:
$ sftp zahn@host1
Connecting to host1..
zahn@host1's password:
sftp>
When the sftp is ready to accept commands, it will display a prompt sftp>. In the sftp manual page there are a complete list of the commands which the user can use; among them there are:
quit
Quits from the application.
cd directory
Changes the current remote working directory.
lcd directory
Changes the current local working directory.
ls [ -R ] [ -l ] [ file .. ]
Lists the names of the files on the remote server. For directories, the contents of the directory are listed. When the -R option is specified, the directory trees are listed recursively. (By default, the subdirectories of the argument directories are not visited). When the -l option is specified, permissions, owners, sizes and modification times are also shown. When no arguments are given, it is assumed that the contents of . are being listed. Currently the options -R and -l are mutually incompatible.
lls [ -R ] [ -l ] [ file .. ]
Same as ls, but operates on the local files.
get [ file .. ]
Transfers the specified files from the remote end to the local end. Directories are recursively copied with their contents.
put [ file .. ]
Transfers the specified files from the local end to the remote end. Directories are recursively copied with their contents.
mkdir dir (rmdir dir)
Mac terminal commands ip. Tries to create (destroy) the directory specified in dir.
Sftp supports glob patterns (wildcards) given to commands ls, lls, get, and put. The format is described in the man page sshregex.
Scp Ssh File
Since sftp use encryption there is drawback: the connection is slower (about a factor of 2-3 to my experience), but this point is of marginal interest considering the great security benefits.
SCP
Ssh Disable Sftp Scp
Scp (Secure Copy) is used to copy files over the network securely. It is probably the simplest way to copy a file into a remote machine. Let's suppose you want to copy the file filename contained in the directory local_dir to your account myname on the directory remote_dir on host host1. Using scp you could enter from the command line:
$scp local_dir/filename myname@host1:remote_dir
In such a way the file filename is copied with the same name. Wildcards can be used (read more about those from sshregex man page). The command:
$scp local_dir/* myname@host1:remote_dir
copies all files from directory local_dir into the directory remote_dir of host1.
The command:
Sftp And Ssh
$scp myname@host1:remote_dir/filename .
copies the file filename from remote_dir on host1 to the local directory.
Sftp Vs Scp
Scp supports many options and allows copies between two remote systems as in the following example:
$scp myname@host1:rem_dir/fname myname@host2:another_dir
Obviously, using scp, you must know the exact directory tree of the remote machine, so in practice sftp is often preferred.






